How does VPN Work? Technical VPN Workflows for Phone, PC, Wifi Explained

With more and more people paying attention to online privacy and security in recent years, VPN service has gradually become a basic application. Then how does a VPN work? How safe it is? Is there any difference between VPN apps? How to choose a reliable and secure VPN?….
VPN is the abbreviated name for “Virtual Private Network”. As the full name implies, VPN is a tool to build and deliver users a private and virtual internet connection. And it actually works in this way, aiming to help people achieve more secure and anonymous web surfing and still circumvent geo-blocking.
We are now living in a world full of censorship, monitoring, and restriction, be it in the physical or cyber world.
When we sit in front of a PC or pick up our phone for web browsing, chatting, emailing, commenting, file sharing, and streaming at our office or home, many pairs of eyes – from the internet service provider (commonly known as ISP), government and corporation – are watching at our behaviors and data silently.
When we are out with a convenient public Wi-Fi connection in the coffee shop, shopping mall, hotel, and so forth areas, besides common legal governmental censorship, WiFi provider and even nefarious hackers are still here, probably tracing and selling your data to the advertiser, stealing your personal information to cause further privacy leakage and financial loss.
When we live in or transitorily move to a region with strict online censorship, e.g China, Russia, and Saudi Arabia, local IP addresses are naturally forbidden to access certain social & political media, porn & torrent sites, and Netflix-alike streaming services.
All of these limits make us feel unfree and risky, being eager to break up their self-directed suppressions and threats. And that’s where VPN comes in.
After you have a rough idea o what is VPN and why use a VPN, let’s take a deep dive into the workflow of a VPN.

How does VPN Work? It Depends on What VPN You’re Using, or Tend to Use
To begin with, let’s have an overall look at the two types of VPN in the market.
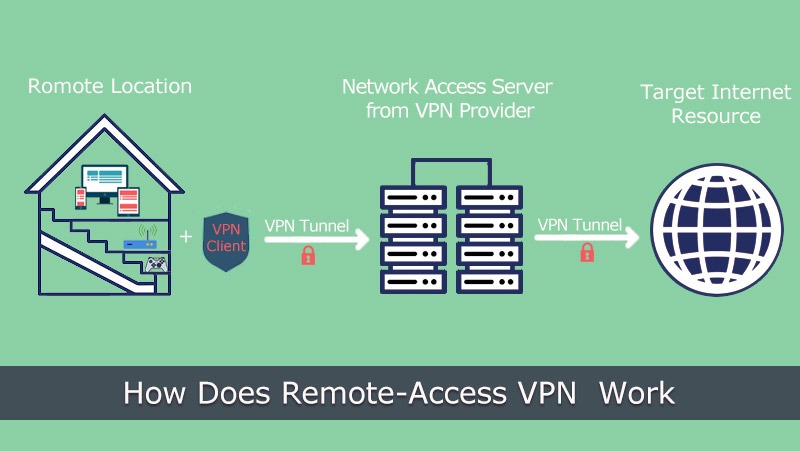
1. Remote Access VPN
It describes such kind of VPN service that allows you to connect and access a remote private server with encryption. Many companies leverage such business remote access VPN to build up a secure connection between their own network and the remote workers’ device, being a boom during the COVID-19 pandemic in recent two years. General consumer-grade VPN services actually belong to this remote access VPN, too, enabling the service user to use their protected network to do online acts with all data encrypted and hidden from other parts.
2. Site-to-Site VPN
Site-to-Site VPN, sometimes called Router-to-Router VPN, is a primary category referring to VPNs that establish a secure connection between multiple endpoints in different locations. Thus, these location-based users are capable of accessing each other’s resources and doing file sharing in the same network. It’s widely applied in companies that have many branch offices and need to cooperate often.
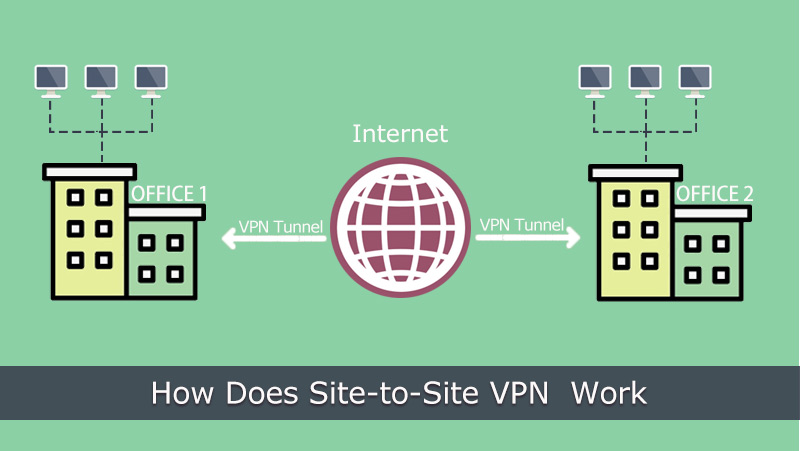
Site-to-site VPN can be furtherly subdivided into intranet-based site-to-site VPN and extranet-based site-to-site VPN, the former of which combines the different LANs into one network named WAN/Wide Area Network while the latter of which connects the LAN of company’s public internet with other out-company parts to share information.
Differences Between Remote Access VPN and Site-to-Site VPN
In brief, remote-access VPNs are commonly leveraged for both individuals and corporations and usually, the client setup is necessary for every customer user in demand, whereas site-to-site VPN is a company-level tool that has no client app to install and doesn’t require every participant to conduct the client software setup.
As to the security method to encrypt VPN tunnels, remote-access VPN accepts SSL and IPsec while site-to-site only supports IPsec (another MPLC protocol doesn’t feature data encryption). Furthermore, the site-to-site VPN permits multiple user’s traffic to flow through any VPN tunnel.
Some Other VPN Types You Are Bound to Encounter
According to the VPN’s actual user scenario, protocol, feature, and cost, you may come across many other VPN names during the information-digging process, such as VPN for business, enterprise VPN, customer-grade VPN, VPN app/desktop software/extension, cloud VPN, router VPN, multi-protocol VPN, SSL/IPsec VPN, no-log VPN, and free/pro VPN. In all probability, they are remote-access VPNs.
Is VPN Application Safe and Do I Really Need It?
For general customers, even after making how does VPN work clearly can’t they reach a decision on whether it’s reliable and why they need it.
At first, VPN is mainly used by those who want be anonymous online for better online privacy, access geo-locked sites and also download torrents. If you happen to be the one, especially who are banned for visiting certain websites, running a VPN is undoubtedly the best way out.

As of VPN’s security concern, everybody should know that it’s different between applications. To judge whether a VPN is safe not not, you are suggested to confirm the VPN protocols it supports, the encryption algorithm and the log policy. A solid VPN must leverage or develop at least one trustworthy protocol, apply a high-grade encryption, strictly perform zero-log policy to lock and protect user data.
8 Mainstream VPN Security Protocols You Must Know
The protocol is crucial for a VPN because this in-VPN tech determines the encryption standard for the whole data transmission. However, since the priority thing varies from one protocol to another, no matter when you are selecting any single-protocol VPN service or picking the one within a multi-protocol VPN, you’d better figure these items out in advance so that you can achieve the desired VPN performance easily.
Below several common VPN protocols are displayed, with their pros and cons listed respectively.
PPTP is a PPP (Point-to-Point Protocol)– based VPN tunneling tech from Microsoft. Being added into Windows systems since Windows 95, this old VPN protocol is really long in the tooth. However, the encryption of this veteran is too basic that anyone who requires VPN routing with the strong ability to lock data is not suggested to choose it. Instead, if you care more about (faster) connection speed rather than data encryption, PPTP is a good bet to standby.
Pros: Wide compatibility, user-friendly, truly cheap, fast speed, unblock (VOD/TV) content
Cons: 128-bit encryption support only (it means poor security), less reliable, firewall unfriendly
2. L2TP/IPSec – Layer 2 Tunneling Protocol
L2TP is a dedicated tunneling protocol made for virtual private networks and ISP service delivery. As the successor of PPTP, it’s more secure than PPTP but more complex to use and set up. But you have to know that by reason this protocol doesn’t support encryption from the very beginning, it’s usually paired with another security protocol called IPsec to deliver users both good speed and data protection.
Pros: Excellent security with AES 256-bit key encryption, wide compatibility, easy to configure, stable connection
Cons: Not ideal for China/Iran etc. countries with severe online restriction due to fixed ports, slow speed unless being paired with OpenVPN,
1. PPTP – Point-to-Point Tunneling Protocol
3. SSTP – Secure Socket Tunneling Protocol
SSTP is another well-known VPN tunnel form developed by Microsoft. Better than both PPTP and L2TP, it transfers PPP traffic through the SSL/TLS channel (over TCP port 443 that’s used by HTTPS) to obtain a higher level of security and bypass (NAT) firewalls, proxy servers, etc.
Pros: Much secure, easy to configure, the great speed with sufficient bandwidth, get rid of the firewall
Cons: Closed-source protocol, limited compatible device, TCP meltdown, possible connection dropping once the header is changed, easier POODLE attack
4. IKEv2/IPsec – Internet Key Exchange, version 2
IKEv2, developed by Microsoft and Cisco jointly, is the newest version of IKEv series protocols. This widely-used VPN encryption protocol builds Security Association (SA) attribute within the authentication suite IPSec to ensure security, privacy, and speed.
Pros: High and stable performance, multiple high-end ciphers support for a decent level of security, MOBIKE supported to resist network change, simple to setup
Cons: Fewer platforms supported, possibly be blocked by firewall
5. OpenVPN
OpenVPN, licensed under GNU GPL, written by James Yonan and released in 2001, is a notably popular open-sourced and cross-platform VPN product. It not only features creating safe point-to-point or site-to-site connections but also been added into many top VPN’s protocol options to let users enjoy its stunning encryption mechanism and functionality. It specifically gains benefit from OpenSSL library on both encryption and authentication work.
The transports of OpenVPN can be either TCP or UDP. TCP promises reliability while UDP guarantees fast speed (for streaming and online gaming.)
Pros: Strong encryption (with AES-256 bit key and similar), high security, circumvent firewalls, stable connection
Cons: Slower speed with latency
6. WireGuard
WireGuard has a dual identity of the communication protocol and open-source VPN software. As a free VPN, it outperforms both IPsec and OpenVPN for proven cryptography (ChaCha20, Poly1305, Curve25519, etc.), speed and power-saving. It passes traffic through UDP (not HTTPS’s 443 port) only.
Pros: Superior cryptography, easy to set up and use, strong security, fast speed, cross-platform
Cons: Still in development, not so stable, more suitable for Linux, all logs kept with privacy problem, possibly be blocked for only supporting non-443-port UDP, the separate infrastructure needed
7. SoftEther
SoftEther is a relatively new open-source VPN protocol and server software that’s released in 2014. With this client-to-server and site-to-site helper, users can do fast internet connections safely with dynamic IP addresses and all data shielded by first-tier AES-256 and RSA-4096 encryption tech.
Pros: Cross-platform, lightweight, powerful encryption, SSL-VPN Tunneling to steer by firewall, high-speed
Cons: Less stable, many VPNs don’t add support for it
8. Shadowsocks
Shadowsocks is a piece of encryption protocol specifically created and also frequently used by programmers in China to blast through the Great Firewall. This open-source tool came out early in 2012 and works as an intermediary to help connect to SOCKS5 proxy. It’s able to disguise your online behavior by using HTTPS but isn’t embedded with any encryption manner to safeguard the traffic and sensitive information. Moreover, various TCP connection support contributes to the ultra-fast speed.
Pros: Cross-platform, easy to install and use, hard to recognize and block, highly customizable, faster speed
Cons: Less functional (especially on privacy and encryption), only friendly with censorship-heavy countries like China
>> Learn more on VPN Protocols
What’s the Difference Between VPNs?
Enterprise VPN is easy to judge and opt for by the internal tech team with expertise. However, for the general public with less knowledge on computing and VPN-related things, it can be tough to sift through the scattered VPN programs.

Here some key differences between VPN services are shared to the newcomers:
- – Server supported countries and regions: The server amount and geo-coverage degree of each varies from VPNs. Still, the servers’ quantity is not 100% proportional to that of nations. For example, VPN a has wider country support while less servers built-in.
- – Platforms: From hot computer, mobile, and smart TV, to router, gaming console and browser, every VPN gets its own way to accept them.
- – Simultaneous Connection: Most VPNs limit the maximum connection at the same time, like 3 and 6, while A smaller portion of VPNs don’t restrict the number of connections.
- – Protocol embedded: Although we have listed eight top-used VPN protocols above, no VPN supports them all, but select one, two or more that work perfectly on their apps.
- – Encryption approach: VPN encryption is front and center if data protection and anonymity are the priorities. You should check out whether this is encryption and what it really is.
- – Site-unblock ability: Political content, social media, torrent and porn sites are relatively easier to unblock. However, streaming services like Netflix/Disney+/BBC iPlayer/Amazon Prime are more complex to handle. Most VPNs more or less have issue with certain steaming sites.
- – Log policy: If encryption prevents data leakage from ISP and government, log policy determines whether your data is collected by the VPN provider itself for further usage. No-log policy should be a must-have!
- – Extra features: For more flexible web surfing, some VPNs are equipped with other functions like split tunneling, kill switch, ads blocker, and real-time speed tester.
- – Price: Premium VPNs tend to provide their services with a certain period of subscription, for instance, one-month plan, 6-month, 1-year, or even 2/3-year plan. Surely the longer the cheaper.
- – Refund: VPNs regularly adopt money-back customer service from 7-day to 45-day.
How to Choose the Best VPN?
After knowing about how does a VPN work and the differences, it’s time to step into how to choose a suitable VPN service. There are about two to three hundred VPN client programs for PC and mobile. In order to pick the best VPN for your daily or business usage, you are suggested to:
☞ Think twice to confirm the prime reason for a VPN
☞ Visit the VPN’s official site and check its full features, server locations, compatible platforms and price.
☞ If it’s very competent to meet your key demand literally, search and browse its word-of-mouth online from TrustPilot, G2, Reddit, or similar review/forum/community results.
☞ Have a test on it with a free trial version (if there is) or the shortest purchase plan (usually 1-month).
☞ After the real test, you will have a better understanding of quality VPN service and how to choose the best VPN rightly.
ENDING
As the informational article goes to an end, you must have a brief idea on how does VPN work, the crucial differences between VPN services, and the normal software selection process. As long as you don’t do something illegal, applying a VPN to hide your privacy, to stay safe on the web, and to access online resources without geo-restriction.
 Vic Knott
Vic Knott  2022.02.28
2022.02.28 










